Security in a Digital World

Security challenges relating to IT are typically thought to be within the realm of the IT organization and rarely assume importance, enough to be the priority of senior management until eventuality strikes in the form of a major cybersecurity event. Such activities are typically delegated to the IT team who perform them in a transactional manner, possibly with old fashioned and transactional protection mechanisms that may not really tie in to the organization’s management and governance processes. They work in siloes, It is therefore not hard to imagine the implications especially in the context of today’s challenges, where enterprises are constantly exposed to digital risks that has the potential to cause several tens to hundreds of million dollars in lost assets or data.
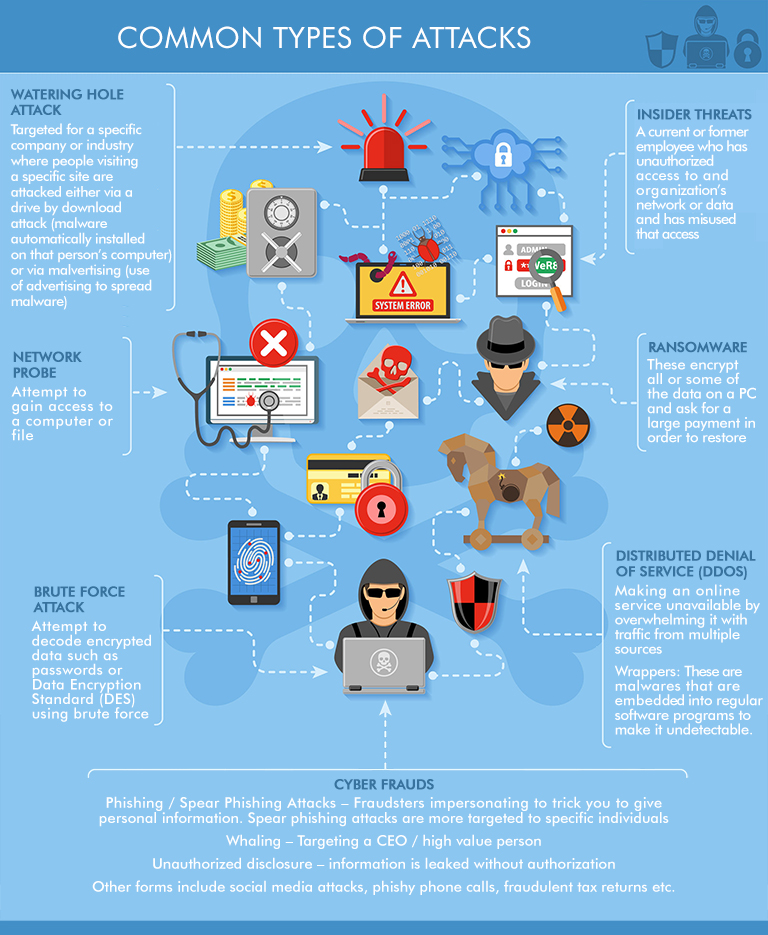
We’re all familiar with the great repercussions that cyber-attacks can have on any industry. The manufacturing industry is one of the most frequently hacked industries next only to healthcare. In a recent Cyber security intelligence index, Automotive accounted for close to 30% of total attacks in the manufacturing industry. Financial services came in third place. Again, government, public sector and infrastructure are also likely to have massive consequences because of attacks. Most attacks are financially motivated, and hence corporate networks and especially sensitive information or intellectual property that is under major threat. There are several new, sophisticated attacks that bypass standard security firewalls, malware and intrusion detection systems and pose a threat to the core operations of the enterprise. The attackers typically focus on stealing or profit from reselling intellectual property. Other attackers want to focus on creating chaos and disrupt operations simply to gain public attention.
It is a no brainer that enormous damage will ensue a cyber-attack literally crippling a business. The number and types of attacks will only grow with technologies such as IOT, AI and cognitive. As companies embark on their digital journeys, cyber security must be a key consideration to protect businesses and people within. The stakes are therefore very high.
GOOD PRACTICES TO MAKE ENTERPRISES ATTACK PROOF

• Organization and Governance : Enterprises should create and execute a strong governance framework that has the sponsorship of senior management. Some enterprises have created a governance committee comprising of key stakeholders from various departments, including key stakeholders from corporate security and IT. Several enterprises have created the position of a CISO (Chief Information Security Officer) to oversee and manage all the cyber security initiatives.
• Structure and program details : Enterprises typically start by creating an inventory of all the types of information in the organization and where it is located. This is typically segregated under several categories such as sensitive, high value, confidential etc. This helps to create a different type of treatment in terms of how it should be protected and governance. Such governance will also include policies on where certain information should or shouldn’t reside, mapping data flows, defining retention rules etc. This will help the organization to put the highest level of protection to the most valuable data.
• Investing in technical controls : Enterprises do invest in several technology solutions to mitigate risks and protect their assets. However, such investment must be constantly reviewed for its completeness, relevancy to changing threats, and needs to be continuously updated to suit. This includes network security (wireless network security including a multi layered next generation firewall), secure remote access, protection of data and information assets, backup, updates, recovery, access control, user account management and BYOD policy based on risk assessment. Asset management policies must be enforced whereby only authorized software and authorized assets are deployed on a company network and regular inventory must be taken for the same.
• Comprehensive Cybersecurity awareness and training : Despite enterprises investing significantly in several cyber security solutions, they are still vulnerable as a lot depends on how much employees understand and are sensitive to taking precautions. For example, employees could erroneously open suspicious mails without realizing that they may be compromising the integrity of their asset or data. One of the most important element in this journey is that of training and awareness creation. This cannot be a one-time activity, but should be almost embedded in every employee’s DNA. Such trainings should be made mandatory and implementation of the same should a key KPI of every employee. Every employee should be made aware of their roles and responsibilities with respect to cyber security.
• Regular vulnerability assessments and reporting : This must be a timed process that takes place irrespective like any other process irrespective of whether there is any suspected compromise. The results from such assessments help enterprises decide where there may be any remote possibility of vulnerability and put in place proactive measures to de-risk.

INCIDENT RESPONSE
The organization and governance elements should include how incidents will be managed in the quickest possible manner including detection of a threat before it spreads to how mitigating losses to the extent possible. This should include clear guidelines with respect to the management and co-ordination of responses in the event of any incidents including involvement of the legal counsel to appropriately respond.
While digital presents a huge potential for innovation and better financial performance, it brings with it a set of challenges that could pose as real threats to an enterprise. Creating a powerful execution plan that builds resilience from impending attacks is critical for business continuity and growth.













